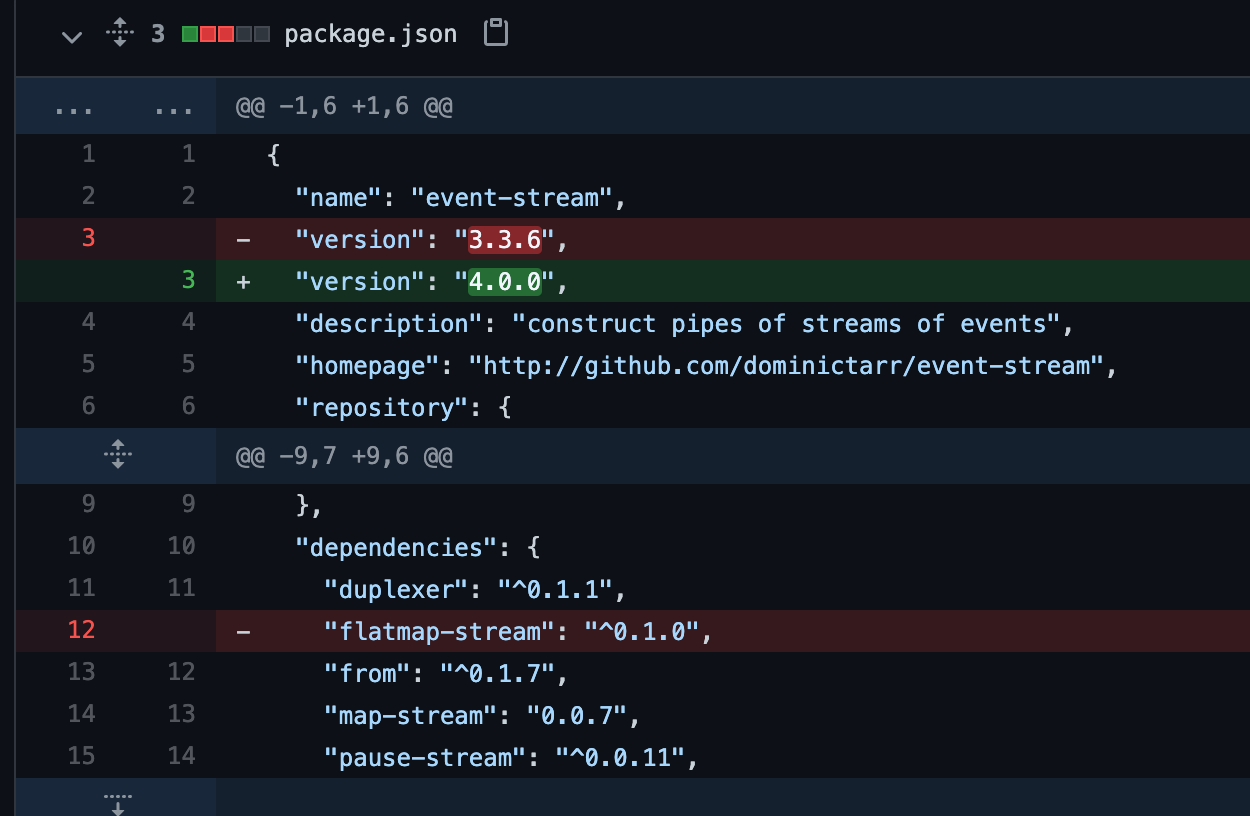
Metadata Analysis of flatmap dependency supply chain attack
Investigating future model detection mechanisms for open source project repositories
There’s been hundreds of software dependency supply chain attacks exploiting a range of vectors in the past, with great effect. The July 2020 paper by Marc Ohm et al describes that on average a malicious package is available for 209 days. (𝑚𝑖𝑛=−1,𝑚𝑎𝑥=1,216,𝜎=258,𝑥̃ =67) so naturally, any method to reduce this...
[Read More]